3.5 Linking Accounts
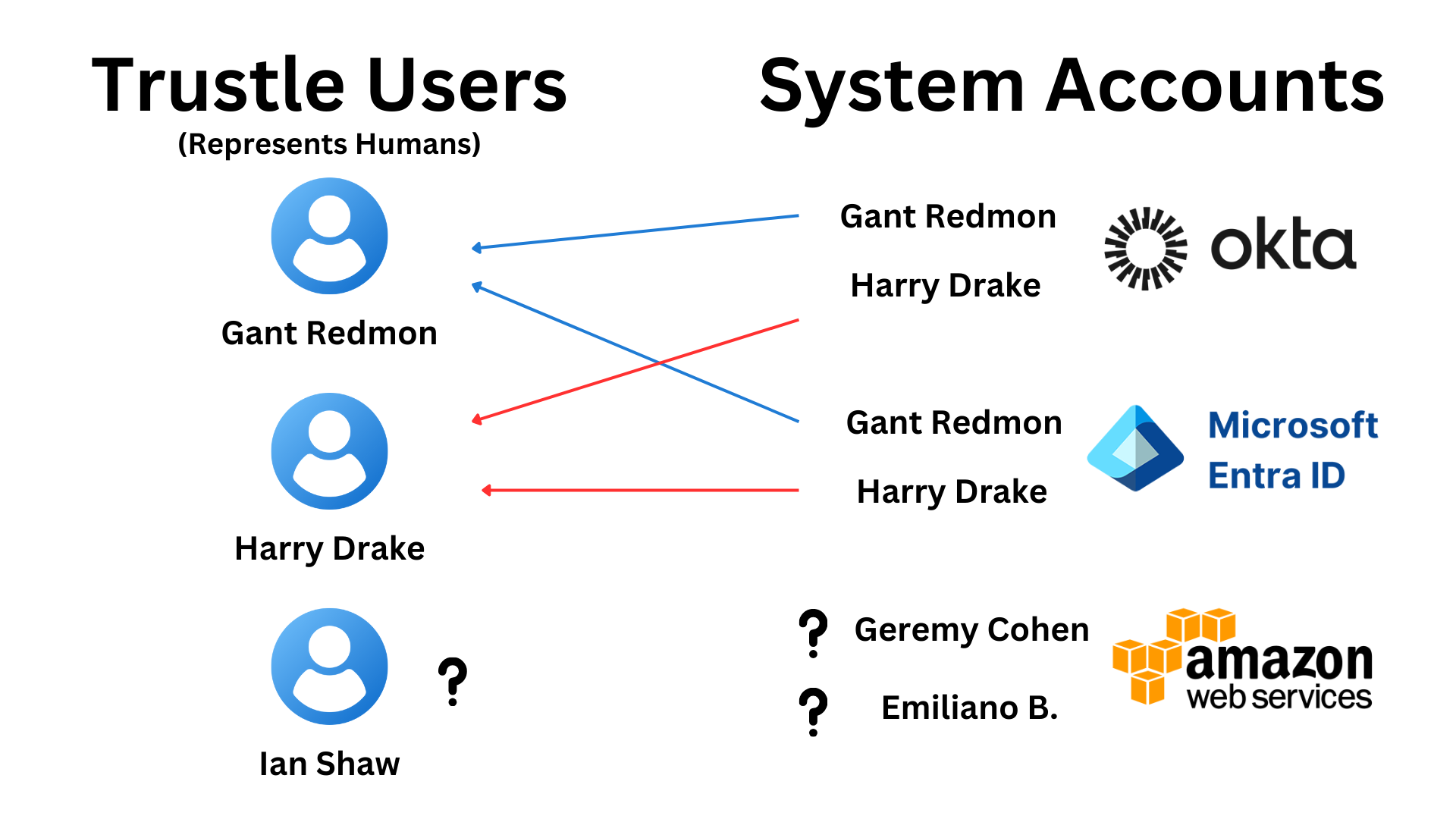
The graphic above displays a simplified view of how Trustle links "Trustle Users" with "System Accounts". This is a critical first step for Trustle to understand which employee in an Organization owns an account on a System (Azure, AWS, etc.). We can see in the graphic that there are 3 Trustle Users, as well as 3 different Systems, each with 2 System Accounts available.
Important: Trustle Users represent human employees in your company.
Gant Redmon and Harry Drake, our Trustle Users, have Accounts on Okta and Azure. These Accounts need to be linked to their associated Trustle User, which we can see with the blue and red arrows. Once each Trustle User is linked to their Accounts, Trustle now knows who owns which Account. This is essential for any Just-In-Time action which moves accounts in and out of groups.
Another important aspect of linking Accounts is to see if any Accounts in the System are orphaned, which means they have no owner. We can see in the graphic that the AWS Accounts Geremy Cohen and Emiliano B. do not have a Trustle User to link to. This means they are orphaned accounts, and are a red flag to your Organization.
Finally, we have the Trustle User Ian Shaw, who does not have any Account on the Systems. This is alright, as employees don't necessarily need to have accounts. This could prompt some questions for that employee, like why does he not have any accounts?
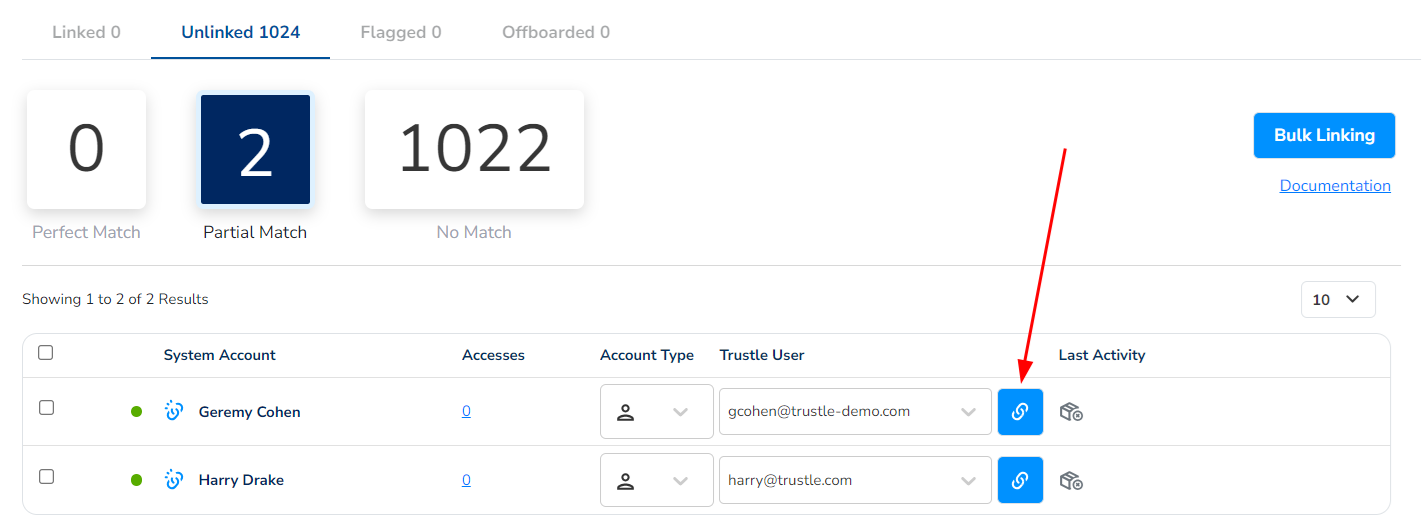
Here is what Account linking looks like in Trustle. To summarize Account Linking:
Linking Trustle accounts to external tools like AWS, GitHub, and Google Workspace is crucial for managing user permissions and identifying unused accounts, which pose significant security risks. These dormant accounts can be exploited if not properly monitored and managed. By integrating Trustle, organizations gain visibility over all accounts, enabling them to quickly detect and deactivate unused ones, thereby mitigating potential security threats. This integration also supports Just-In-Time (JIT) access and adherence to Zero Standing Privilege (ZSP) and Least Privilege Access (LPA) principles. This ensures users have the necessary access without excess privileges, which enhances overall security and compliance.